More Transparency Needed For Government's Use of National Security Powers For Data Requests From Companies

[Graphic by └¤░─├┼┐¬¢▒¢ß╣¹ based on ]
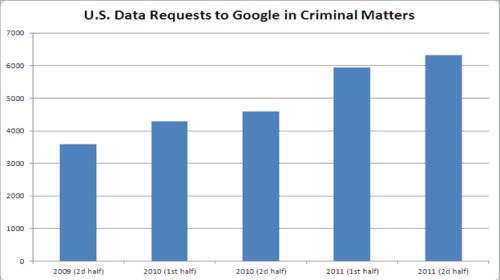
Most of the attention surrounding has focused on copyright protection and government censorship. The quick summary: copyright takedown requests and government censorship have increased. But the report is perhaps more notable because of its importance for our privacy. The report reveals that the U.S. government asked Google for data on its users 6,321 times during the second half of 2011ÔÇöa 75% increase from two years ago.
ItÔÇÖs hard to understand just what that number means. GoogleÔÇÖs that its transparency statistics do not cover ÔÇ£all categories of data requests from the government,ÔÇØ but focus primarily on ÔÇ£requests in criminal matters.ÔÇØ This means that the statistics very likely ╗Õ┤Ã▓ÈÔÇÖt cover the most troublesome surveillance authorities passed after 9/11, such as National Security Letters, Patriot Act orders under Section 215, and the FISA Amendments Act of 2008 (which replaced and in some ways expanded the Bush administrationÔÇÖs warrantless wiretapping program). (These national-security powers are now used in criminal investigations, too.)
How many times has the government tapped Google using those new surveillance powers? We ╗Õ┤Ã▓ÈÔÇÖt know, but we do know that the government has relied on those powers more and more since 9/11 with relatively little public oversight and even less meaningful judicial review. It wouldnÔÇÖt be surprising if those unreleased statistics dwarf the very limited statistics that Google released.
Of course, Google should be applauded for releasing its transparency report. As we store an ever-increasing part of our private lives on the servers of companies like Google, we must demand transparent privacy policies so that we can have an informed debate about the limits of government access to our private information. Other companies should follow GoogleÔÇÖs lead, but they all should release even more information, accounting for all forms of government data requests for or acquisitions of the information that we entrust them to store.

